While you may worry about external sources breaching your organization’s data, insider threats remain the most dangerous and damaging. A study conducted by the Carnegie Mellon University Software Engineering Institute showed that incidents caused by insider attacks were costlier or more harmful than outsider attacks.
Insider attacks mostly stem from corporate and employee neglect. People may unintentionally expose a company’s weak spots, making them vulnerable to external threats. Because of the lack of precaution, insiders unknowingly let outsiders easily access sensitive company data. Consequently, hackers can steal corporate data and cause monetary damage.
When it comes to safeguarding your organization against attacks, User Behavior Analytics (UBA) effectively exposes suspicious attacker activities. UBA technology focuses on user activity to detect what it considers ‘normal’ behavior or risky behavior on a network.
As Verizon reports in its annual Data Breach Incident Report (DBIR), thousands of incidents and breaches continue to be reported every year. Such attacks target personal information stored by an organization for financial gain or public defamation.
What Is UBA?
User Behavior Analytics (UBA) can be described as the process of collecting, tracking, and assessing data on the events generated by your users through their daily activities. Behavioral analytics software analyzes historical data logs, such as network and authentication logs stored in SIEM and log management systems. It then uses such information to identify patterns of traffic or user behaviors, both normal and suspicious.
UBA technologies work by organizing the data into logical, useful analytics reports. It then utilizes machine learning, algorithms, statistics, and probability to highlight the behaviors of threat actors. Insider threats are the hardest to catch and have the potential to be the most damaging. UBA tools arm organizations with specific data to detect suspicious patterns that may indicate fraud, credential theft, and other malicious activities.
Now, you must be wondering, “Isn’t anti-malware software sufficient to prevent data breaches?” Well, not quite. Hackers have become clever with their infiltration techniques. They can create specially crafted malware that goes undetected. They can also use phishing, SQL injection, or install RATs (remote administration tools) and easily gain access to an organization’s network.
User Behavior Analytics is coined from Behavior Analytics, a concept that originated in the world of marketing. Products like Google Analytics provide organized reports of server activity logs, granting marketers greater insights into who did what while visiting their websites. This insight into user interaction helped marketers optimize their websites for maximum conversion levels, consequently leading to higher revenues.
Over time, the same information proved to be crucial and prevalent throughout all the departments in an organization, including human resources and sales. The data was particularly necessary for the security department to help analyze suspicious behavior and protect against potential threats. Organizations now use data from behavioral analytics software to optimize employee workflows and understand employee and team engagement.
User and Entity Behavior Analytics (UEBA) is a term that evolved from UBA. It adds “Entity” into the mix to indicate malicious behavior by humans and devices, endpoints, networks, and applications. According to Gartner, which coined the term UEBA, the behavior of these entities, particularly users, devices, and system accounts, can reveal anomalies, even when they occur over longer periods.
UEBA uses machine learning to build baselines for every entity in the network and then detects deviations from the norm. The system assigns the anomaly a score indicating the intensity of the threat. This way, security officials can review daily alerts, watch out for malicious users and take preventive action.
SIEM Vs. UBA
User Behavior Analytics and Security Information and Event Management (SIEM) systems are closely related. However, there are distinct differences between these two security systems. SIEM provides real-time analysis of security alerts to anything and everything that happens within your infrastructure. It collects log and event records from all of your other security systems, including firewalls, network switches, servers, etc., in a centralized location and analyzes the data.
Unlike SIEM systems, UBA doesn’t focus on perimeter systems and OS logs. Rather, it focuses on users, user accounts, and user identities. These are specific event data with historical activity data from the user, application, website, and machine. As a result, the data collected is more accurate and provides more prevalent alerts.
SIEM applications use pre-defined rules and inputs to analyze behavior in near real-time. While they work, they can be bad at spotting anomalous behavior from hacker activity or insiders abusing their access. UBA, on the other hand, utilizes a long-term approach by analyzing user behavior over extended periods and only draws attention to truly anomalous activity.
Why Your Organization Needs User Behavior Analytics
Cybercrime has been on the increase in recent years, and companies continue to lose millions of dollars every year. If the Snowden, WikiLeaks, and Target breaches prove anything, it’s that security methods quickly become obsolete. Employees can share passwords with friends and family members, your firewall can be bypassed, and a disgruntled employee can give out sensitive credentials.
This is especially true for larger corporations with porous IT perimeters that prove difficult to manage and oversee. This level of uncertainty in the world of business requires a more robust approach to safeguarding company data. A UBA system helps detect the presence of a hacker who has managed to successfully infiltrate your network, minimizing potential damage.
Benefits of UBA to an Organization

Monitor and Protect Against Risks
User Behavior Analytics security system can uncover outside threats that have penetrated your organization’s perimeter or user behaviors that are threatening company operations. They provide a better chance of pinpointing where the security breach originated from.
For instance, if the breach was internal, you can find the exact moment a user accessed specific material, document, or website. You can determine the time wherein the malware was injected. If the attack was external, you can track and monitor the user’s movements throughout your organization’s network and devices.
Detect Insider Threats
You can never tell when an employee or group of employees would go rogue and do something malicious, like steal data using their own access. UBA helps your security specialists to detect potential risks early and take the necessary preventive measures. You can trace privilege abuse and policy violations made by your own staff.
UBA/UEBA systems can effectively detect threats originating from human behavior. These threats include guessing passwords, intentionally planting malware, or leaking sensitive data as a legitimate user. You can also use an employee time tracking system to help you monitor activities closely.
Detect Compromised Accounts
A user can inadvertently download malware due to a phishing attack, or a legitimate account could be spoofed. UBA/UEBA can help expose the compromised accounts and track down the authorized user.
As noted, UBA leverages machine learning, statistics, and algorithms to create a baseline profile or pattern. Any action that appears out of the ordinary will flag the system and notify the administrator of the anomaly.
Greater Visibility for Policy Compliance
Typically, an organization’s policy compliance falls within employee monitoring. Normally, it would be difficult to detect policy violations. UBA systems will send alerts and notifications of unexpected behavior from employees so you can investigate the anomaly.
In other words, behavioral analytics will help you identify those violating company policies and take the necessary disciplinary action.
Encourages Transparency and Accountability
Investing in User Behavior Analytics technologies improves your organization’s transparency since every action and operation is documented. A data expert can use the data to audit how each job was handled. They will identify processes that work and those that don’t. The results will shed light on areas that need optimization. Consequently, managers will have better insights into what can help scale business growth.
Reduces False Positives
SIEM services generate useful information and send reports when security logs detect threats. However, these logs may lack details like what a user did, to which files, and when. UBA detects threats through anomaly scoring. It can filter alerts before they are sent to the security operations team, thus eliminating erroneous reporting.
As a result, security teams can focus on uncovering activities that carry real risks and prioritize response to urgent and complex threats in the organization.
Choosing the Right UBA Tool for Your Organization
Before you invest in UBA software, here are some important factors to consider:
- Is it tailorable to my organization’s needs?
- What are my budget considerations?
- Will it provide the data we need?
- Can it integrate with the organization’s existing system? If so, how well?
- Is threat detection streamlined and efficient?
Ultimately, choosing the right UBA system will boil down to your priorities, concerns, and needs.
User Behavior and Organizational Effectiveness
UBA is a necessary step to tighten your organization’s security. The system helps to detect true anomalies and predict attacks from inside your network. However, there’s more to UBA than just exposing security breaches.
User behavior data can be critical to your organization’s success. You can use the data to review processes within the organization, and then identify and eliminate inefficient processes. Analyzing user behavior also allows you to understand the real impact of a new process and measure the resulting output.
Such insights can be valuable in ensuring that all the company’s earnings are spent wisely, hence reducing wastage and increasing profits. Combined with an employee monitoring tool like Traqq, management will have the upper hand on everything happening within the organization. What’s more, online monitoring tools can help you ensure that your workers are complying with data security policies.
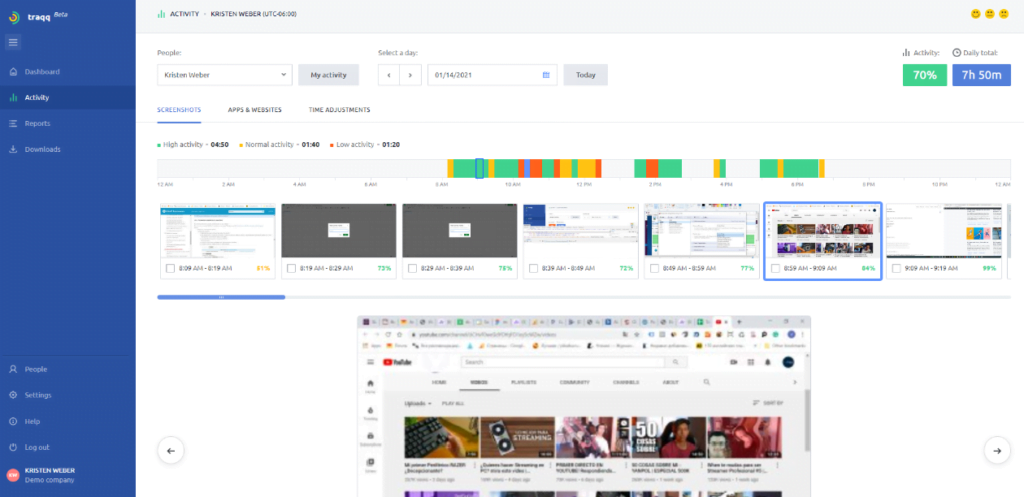
Traqq is a productivity tracking app that lets you monitor the websites accessed and apps used by employees. The tool takes random screenshots and video recordings of a user’s desktop. On the dashboard, you can see what they are doing in real-time. Even so, it still protects your employees’ privacy. The images are blurred to the extent that will make sensitive details (like passwords and private messages) illegible. You will only have an idea of what your employees are doing.
Another thing that Traqq does is create a report of the websites and apps that your workers access. The tool even creates a visual representation of what eats up the biggest chunks of their time. This way, you will know if they’ve been accessing sites or apps that may harm the security of the organization’s data. The best part about Traqq is it is free. You can download and use all of its features at no cost.